
Your hacked WordPress site must be clean up properly. Otherwise, it allows hackers to get in back to your website again. Because most of the hackers create backdoors as the first task when they are hacking a website. Those created backdoors can bypass normal authentication in your site. Hence if you are not clean up your hacked WordPress site properly, it allows for security vulnerabilities in the future.
As WordPress website owners, you should know how to prevent further risk of being hacking the website by backdoors created on your website. This article gives you clear guidance on how to find a backdoor created in your hacked WordPress site and methods you have to apply to fix them. Hence this article is more important to refer to by all WordPress site owners.
What is Backdoor?
This is a technique of bypassing normal authentication on the website and obtaining access to the server remotely. However, it can gain access to the server while remaining undetected. Most hackers create backdoors initially and they can gain access even after remove the affected plugins. As well as backdoors often survive the upgrades and it is essential to clean up the website properly. Unless your website in under the security risk.
Backdoors can function in different ways. Some backdoors can create hidden admin username while some complex backdoors allow hackers to implement PHP code sent from the browser. As well as some backdoors have a full fledge UL and they send emails as the server, perform SQL queries, and some tasks they want to do.
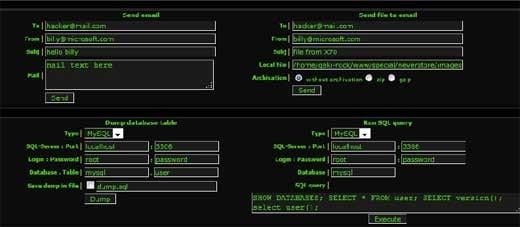
Where is this code hidden?
It can mention some common locations in which hackers are installing backdoors usually. As WordPress site owners, you should have clear guidance regarding this.
Themes
– Most cases hackers do not use your current theme to install a backdoor. It needs a code to survive core updates. Hence, most hackers use old Kubrick themes sittings and other inactive themes to locate those codes. Hence, it is better to remove your all inactive themes from the WordPress site.
Plugins
– Normally users will not pay attention much on plugins and users are less likely to upgrade their plugins. Then they survive the upgrades. Another thing is that some poorly coded plugins have their own weaknesses, to begin with. Because of these reasons WordPress site plugins are one of the best locations for hackers to install backdoors.

Uploads directory
– Surely most users will not check the upload directory. You just upload the image and use it on your post. Thousands of images will have in your upload directory normally. Then hackers can locate a backdoor among these thousands of media files very easily and difficult to note it also due to a heavy amount of images. And most users do not use monitoring plugins like Sucuri and users are not monitor upload directory regularly.
Wp-config.php
– This is also a major target location by hackers to install a backdoor. Most users also check this first.
Includes folder
– /wp-includes/folder is also one of the places which can find backdoors. However, most users do not check this also. Hackers will keep more than one backdoors file to ensure their access again to the website normally.
Most of the cases the backdoor is disguised like a WordPress file. It can be found in some instances the backdoor in the wp-includes folder which has named as wp-user.php. However, it does not exist in the normal install. Because there can be a file in the wp-includes folder as user.php and not as wp-user.php. As well as it will find out a PHP file named hello.php in the upload folder. It can be disguised as the Hello Dolly plugin.
The backdoors can be named as wp-content.old.tmp, data.php, and php5.php. The backdoor does not have to end with PHP. The reason is that the backdoor has a PHP code in it. Also, it can be a zip file. These files have encoded with base64 code. Normally those codes are performing all sort operations such as add spam links, add additional pages, and redirect the main site to spammy pages.

The current version of the WordPress site has no known vulnerabilities. Normally hackers search an exploit in a third-party plugin or script and then give them access to locate the backdoor. A poorly coded plugin can allow user privilege escalation and if your WordPress website has open registrations then hackers also can register for free. After that hackers can upload the files. Another thing is that your authorizations should be compromised. Also, you may use a bad hosting provider.
How to find and clean the Backdoor?
Now you will have a good understanding of the backdoor and the locations where you can be found them. Actually finding a backdoor is the difficult task that you have to do. For that, you can make easy your finding task by getting the support from a malware scanner WordPress plugins. Sucuri can be recommended for it. However, you can use the Exploit scanner. However, you can delete the plugin directory and then reinstall the plugins from scratch. This also one of the best thing you can do and you can save you time. As it does not require much time to spend.
Search the Uploads Directory
If the scanner finds out a rogue file in the upload directory and you are familiar with SSH, you can write the below command.
find uploads-name “*.php”-print
If your upload directory has a .php file, it is not good to remain the file further. If so, you need to remove it. In most cases, the folder will be designed as a media file.
Delete inactive themes
Most probably Hackers target inactive themes to locate backdoors. Because of that, it is good to delete all inactive themes including default and classic themes. Then you are not required to worry by searching for backdoors on the inactive themes. Because now you remove them already from your website. So this saves your time and eliminates a potential point of attack.
.htaccess file
The direct codes can be added in the .htaccess files. You have to delete the file and then it will recreate itself. But if it does not go to the WordPress admin panel you have to do below steps to do it simply.
- Settings and then go for Permalinks.
- Click on the Save button.
Then deleted .htaccess file will recreate.
Wp-config.php file
You have to compare this file with the default wp-config-sample.php file. If you can see something different between two files then you can just remove the Wp-config.php file.
Database scan for Exploits and Spam

Hackers will create numerous safe points targeting the full database. Hackers will store bad PHP functions, new administrative accounts, SPAM links in the database. As well as you will not see the admin user in your user’s page. But you will see there are three users and you can see that two chances you are hacked. Exploit scanner plugin or paid version of Sucuri if you do not know SQL to do your task.
You have to open your browser in an incognito mode and see whether the hack comes back. Because in most cases logged out users will see the hack and not by logged in users. Also, it is better to change the browser’s user agent as Google. Because the hackers will target only the search engines. If you require to know 100% that there is no hack, then you can delete it and restore it to the point you suppose that the hack was not there.
How to prevent hacks in the future?

You have to maintain strong backups such as VaultPress and BackupBuddy. As well as you have to use monitoring services such as Sucuri. Because users are difficult to monitor all things with other tasks practically. Today the Sucuri is a well-recommended monitoring service by large companies such as CNN, USAToday, PC World, TechCrunch, and TheNextWeb. You can further refer to the article on 5 Reasons Why We Use Sucuri to Improve our WordPress Security.
Below are some of the things that you can do to enhance the security of your WordPress website.
Use strong passwords
– You can allow users to use strong passwords. For that, it can use a password managing utility such as 1Password.
2-Step authentication
– It is better to apply two-step authentication. Then the user can verify code from the mobile to compromise the user’s password.
Limit login attempts
– This method is to block the users after a specific number of login attempts. Then hackers cannot test their usernames and passwords combinations
Disable theme and plugin editors
– This method avoids user escalation issues. Then hackers cannot modify the theme or plugins using the WP-Admin.
Password protect WP-Admin
– You can password protect the entire directory and limit access by IP.
Disable PHP execution in certain WordPress directories
– This method, disables PHP execution in the upload directories. Even others are able to upload the file, they will not able to execute the uploaded folder.
Stay updated
– You should make sure that whether your WordPress website is updated to the latest version and upgrade plugins.
The best security method is maintaining backups. So it is essential to keep your backups regularly. But most web hosting companies do not maintain backups for you. Because of that, you must implement the best solution such as BackupBuddy and VaultPress. If something happens to your website like hacking, you have to restore the solution. Also, you can obtain the service of Sucuri and save your problems in WordPress if it has hacked. It will clean up your website by regularly monitoring and protect your website.
Connect with us
We would like to hear about your problems, questions, and suggestions. So feel free to contact us. This is free of charge service that we offer. But we receive thousands of emails per day. So it is impossible to reply to all of them. So we create a Community to help you individually. Go to Community and open help Topic under the relevant category. Please spread this post to your friends by sharing Facebook and other major social media. And make sure to like us on Facebook.