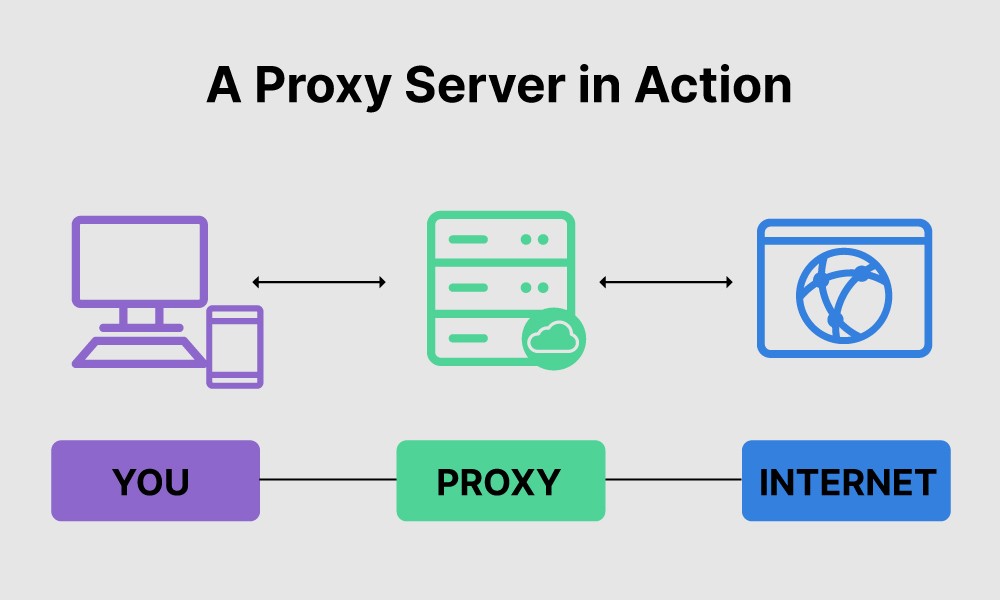
Understanding the Importance of a Private Mobile Proxy Server
One of the primary benefits of using a private mobile proxy server is secure browsing. By routing your internet traffic through a proxy server, you can encrypt your data and prevent it from being intercepted by malicious actors or hackers. This ensures that sensitive information such as login credentials or financial details remain confidential.
Another advantage is anonymous web surfing. When you connect to the internet through a private mobile proxy server, your real IP address is masked, making it difficult for websites or online services to track your location or identify you personally. This anonymity allows you to browse the web without leaving behind digital footprints that could be used for targeted advertising or surveillance purposes.
Additionally, private mobile proxies, like those from https://proxy-seller.com, offer enhanced access to geo-restricted content. By connecting through a proxy server located in a specific region or country, you can bypass geographical restrictions imposed by certain websites or streaming platforms. This means that you can access content that may otherwise be unavailable in your location.
In conclusion, utilizing a private mobile proxy server provides numerous benefits including secure browsing, anonymous web surfing, and access to geo-restricted content. As privacy concerns continue to grow in importance, integrating this technology into your online activities can help safeguard your personal information and ensure a safer browsing experience.
Why Choose a Private Mobile Proxy Server Over other Proxy Types?
When it comes to choosing a proxy server, there are various options available, each with its own set of advantages and disadvantages. However, for those seeking high anonymity and IP authentication, a private mobile proxy server stands out as an excellent choice.
One of the key advantages of a private mobile proxy server is its high level of anonymity. Unlike other proxies that may be easily detected and blocked by websites or online platforms, mobile proxies offer a greater level of stealth. This is because they utilize IP addresses associated with mobile devices, making them appear as regular users accessing the internet through their smartphones or tablets.
Compared to other types of proxies such as data center or residential proxies, private mobile proxy servers provide an added layer of security. With IP authentication, users can ensure that only authorized individuals can access the proxy server. This feature enhances privacy and prevents unauthorized access to sensitive information.
In addition to their high anonymity and IP authentication features, private mobile proxy servers offer convenience and flexibility. Users can easily switch between different locations by connecting through different mobile devices or SIM cards. This allows for seamless browsing experiences across various regions without the need for complicated configurations.
Overall, choosing a private mobile proxy server over other types of proxies provides several benefits including enhanced anonymity, IP authentication, and convenient location switching. These advantages make them an ideal choice for individuals or businesses seeking reliable and secure internet connections while maintaining a high level of privacy.
Finding the Right Provider: Key Factors to Consider
When it comes to choosing a private proxy provider, there are several key factors that you should consider. These factors will help ensure that you find a provider that meets your specific needs and requirements.
One of the most important factors to consider is the reliability and uptime of the provider. A reliable provider will have a high uptime percentage, meaning that their servers are consistently available and accessible. This is crucial for uninterrupted browsing or accessing restricted content.
Another factor to consider is the server locations offered by the provider. The more server locations they have, the more options you’ll have when it comes to selecting an IP address from a specific location. This can be particularly important if you require proxies from specific regions for your online activities.
Customer support is another crucial aspect to evaluate when choosing a private proxy provider. A reputable provider should offer responsive and knowledgeable customer support to assist you with any issues or queries that may arise during your usage of their services.
By considering these key factors – reliability and uptime, server locations, and customer support – you can make an informed decision when selecting a private proxy provider that best suits your needs.
1. Server Locations and Coverage:
When it comes to proxy servers, one important aspect to consider is the server locations and coverage. The availability of proxy servers in different locations around the world plays a crucial role in meeting specific country requirements and ensuring global coverage.
Proxy server locations refer to the physical locations where the proxy servers are located. These servers act as intermediaries between the user’s device and the internet, allowing users to access websites and online content from a different IP address.
Having a wide range of proxy server locations is essential for various reasons. Firstly, it allows users to bypass geo-restrictions imposed by certain websites or online platforms. By connecting through a proxy server located in a specific country, users can appear as if they are browsing from that country, granting them access to regionally restricted content.
Secondly, businesses often have specific country requirements for their operations or marketing strategies. They may need to gather market insights or conduct localized testing by accessing websites from specific countries. In such cases, having proxy servers available in those countries becomes crucial.
Lastly, global coverage ensures that users have reliable and fast connections regardless of their geographical location. By having proxy servers strategically placed around the world, service providers can minimize latency and provide optimal performance for their users.
In summary, when choosing a proxy service provider, considering their server locations and coverage is vital. This ensures that specific country requirements are met while offering global accessibility for seamless browsing experiences.
2. Speed and Performance:
Fast mobile proxies play a significant role in optimizing online activities. These proxies act as intermediaries between users and the internet, allowing for secure and anonymous browsing. The speed of these proxies is essential as it directly impacts the loading time of web pages, file downloads, and overall responsiveness.
Low latency connections are also paramount when it comes to delivering real-time data and maintaining smooth communication channels. Latency refers to the delay between a request being sent from a device to receiving a response from the server. With low latency connections, data can be transmitted quickly, resulting in faster load times for websites, reduced lag in online gaming, and improved video streaming quality.
For businesses relying on online operations or individuals seeking optimal internet experiences, investing in fast mobile proxies and low latency connections can greatly enhance performance. These technologies ensure that data is transmitted swiftly and efficiently, minimizing delays and maximizing productivity.
3. Security Features:
Data encryption protocols play a crucial role in ensuring the security of sensitive information. In this section, we will explore the importance of security features, specifically focusing on data encryption protocols.
Data encryption protocols are designed to protect data from unauthorized access or interception. These protocols use complex algorithms to convert plain text into ciphertext, making it unreadable to anyone without the decryption key. By employing strong encryption techniques, organizations can safeguard their data from potential threats such as hackers or malicious insiders.
One of the most widely used encryption protocols is Transport Layer Security (TLS), which is commonly used to secure internet communications. TLS encrypts data during transmission, ensuring that it cannot be intercepted or tampered with by unauthorized parties. It provides a secure channel for exchanging sensitive information, such as passwords or financial details.
Another important encryption protocol is Pretty Good Privacy (PGP), which is commonly used for email encryption and digital signatures. PGP employs asymmetric cryptography to encrypt and decrypt messages, ensuring that only the intended recipient can read the content.
In addition to these widely recognized protocols, there are various other encryption techniques and algorithms available that cater to different security requirements. Organizations must carefully assess their needs and choose an appropriate data encryption protocol that aligns with their security goals.
By implementing robust data encryption protocols, organizations can enhance their overall security posture and protect sensitive information from unauthorized access or disclosure. These security features are essential in today’s digital landscape where cyber threats continue to evolve rapidly.
4. Pricing Options:
When it comes to pricing options for various usage needs, companies often offer different plans to cater to the diverse requirements of their customers. These pricing plans are designed to provide flexibility and value for money.
One common pricing option is the tiered or tiered-based pricing model. This model offers multiple tiers or levels of service, each with its own set of features and corresponding price. Customers can choose the tier that best suits their specific usage needs and budget.
Another popular pricing option is the pay-as-you-go model. With this option, customers are charged based on their actual usage of the product or service. It provides a more flexible approach as customers only pay for what they use, making it ideal for those with fluctuating or unpredictable usage patterns.
Additionally, some companies offer subscription-based pricing plans. These plans typically require customers to pay a fixed monthly or annual fee in exchange for unlimited access to the product or service. This option is suitable for those who have consistent and regular usage needs.
Lastly, some companies may also offer customized or enterprise-level pricing options. These plans are tailored specifically for larger organizations with unique requirements and higher usage volumes. Customized pricing allows businesses to negotiate terms and conditions based on their specific needs.
Ultimately, the availability of different pricing options ensures that businesses can find a plan that aligns with their budget and meets their varying usage needs effectively.
The Process of Purchasing a Private Mobile Proxy Server
When it comes to purchasing a private mobile proxy server, there are several steps involved in the process. Understanding these steps can help ensure a smooth and hassle-free experience.
Firstly, you will need to find a reputable provider that offers private mobile proxies. There are various companies in the market that offer this service, so it’s important to do your research and choose one that meets your specific needs.
Once you have selected a provider, the next step is to determine the payment method accepted by the company. Most providers offer multiple payment options such as credit cards, PayPal, or cryptocurrencies. It’s important to choose a payment method that you are comfortable with and provides secure transactions.
After completing the payment process, you will typically receive an email containing your account details and instructions for setting up and configuring your private mobile proxy server. This may involve downloading specific software or configuring settings on your device.
During the setup process, it’s crucial to follow the instructions provided by the provider carefully. This ensures that your private mobile proxy server is configured correctly and functions optimally.
In case you encounter any difficulties during setup or configuration, most providers offer customer support services to assist you. You can reach out to their support team via email or live chat for guidance and troubleshooting.
By following these steps – finding a reputable provider, selecting a suitable payment method, setting up and configuring your account – you can successfully purchase a private mobile proxy server for enhanced online privacy and security.